Reduce the risk of browsing the internet or working on a corporate-owned laptop on a public WiFi connection
With more employees working remotely, and now back to traveling for business and connecting to public WiFi in airports or hotel rooms, it is important to revisit the security concerns of working on public WiFi connections.
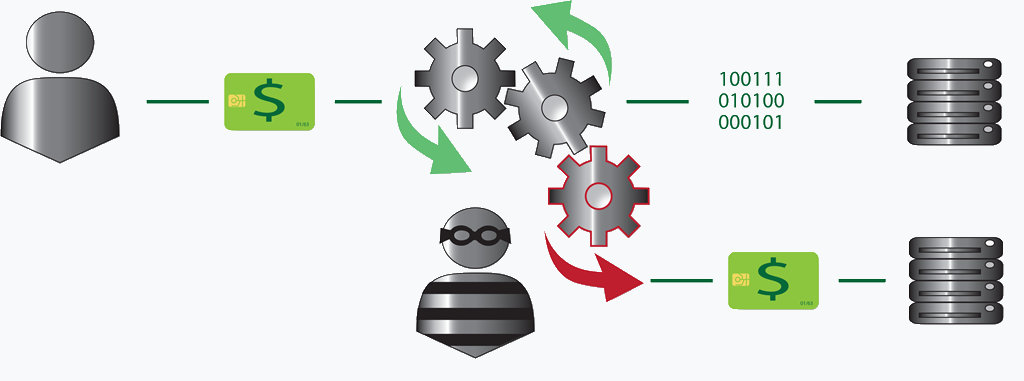
Browsing the internet or working on a public wifi connection can pose several cybersecurity risks to your privacy and sensitive information. One possibility is that the WiFi connection is not secure. Even worse is an imposter WiFi connection, with a similar name to a legitimate WiFi connection specifically designed to trick you into connecting – these are referred to as “spoofed” WiFi connections or “rogue” or “evil twin” WiFi networks.
Once connected to an unsecured or spoofed WiFi connection, you would be vulnerable to Man-in-the-Middle (MITM) attacks. A MITM attack is a form of eavesdropping where hackers can gain access to networks, redirect traffic on a network, and intercept data while in transmission. This could lead to compromised account credentials or loss of other confidential information.
In addition to eavesdropping or altering your private communications, hackers could also inject malicous code into the data stream which the unsuspecting user could then download onto their machine as malware.
Use a VPN Service
One way to protect yourself from these public WiFi risks is to use a VPN service to encrypt your internet connection and protect your sensitive information.
By encrypting your internet connection, a VPN service can prevent hackers from intercepting your data and stealing your personal information or corporate data. A VPN service is different than a Remote Access VPN connection or a Site-to-Site VPN connection. A VPN service allows you to connect to the internet through a public WiFi connection to a server provided by a service that you would subscribe to. When you connect to the VPN service, your device creates a secure connection to the VPN server. All of your internet traffic is then routed through this secure connection, which is encrypted to prevent anyone from intercepting your data.
SyncraTec is committed to helping clients setup cybersecurity protection in accordance with the guidance provided by the Center for Internet Security (CIS) Controls framework, referred to as CIS Controls v8 (ref.: http://www.cisecurity.org/controls/). Browsing the internet via a public WiFi connection would be covered by CIS Critical Security Control 12 — Network Infrastructure Management.
Safeguard number 12.6 cites Use of Secure Network Management and Communication Protocols
Use secure network management and communication protocols (e.g., Wi-Fi Protected Access 2 (WPA2) Enterprise or greater). If you’re not sure if your local coffee shop WiFi is WPA2 Enterprise or greater, use a VPN service to encrypt your connection.
Safeguard number 12.7 cites Ensure Remote Devices Utilize a VPN and are Connecting to an Enterprise’s AAA Infrastructure
Require users to authenticate to enterprise-managed VPN and authentication services prior to accessing enterprise resources on end-user devices. This control states that a VPN connection should be in place prior to connecting to corporate IT resources.
Ask SyncraTec about how a VPN service can be provided for end-users to protect internet browsing on public WiFi networks. SyncraTec is a Managed IT Services Provider in the Philadelphia area focused on cybersecurity, compliance, and business productivity for small businesses.